In IT environments and in certain industries it is very common to hear the importance of Sarbanes Oxley compliance (also known as SOX act), to strengthen the internal control environment and establish controls against financial risk. It is also mandatory to comply with the constant audits that are carried out to evaluate its correct implementation. But what exactly is the Sarbanes-Oxley act?
What is SOX?
The Sarbanes – Oxley Act / or SOX is an American federal law of 2002 which seeks to establish investor confidence after several corporate and accounting scandals. It aims to protect investors by creating internal controls over financial reporting to facilitate the accuracy and reliability of financial information and disclosures.
The law was enacted on July 30, 2002, and establishes a wide range of new standards for public companies, boards of directors and accounting firms. It establishes a Public Company Accounting Oversight Board (PCAOB) to oversee public company auditors.
The law applies to all companies whose shares are traded or offered on US stock exchanges or over the counter in the US and that are regulated by the Securities and Exchange Commission (SEC). It does not apply to privately held companies.
What are SOX controls in IT?
From a technical point of view, SOX proposes a minimum control environment to secure the information systems that support the transactionality of financial information, so that it preserves the principles of availability, confidentiality and integrity of information.
This minimum environment considers the following:
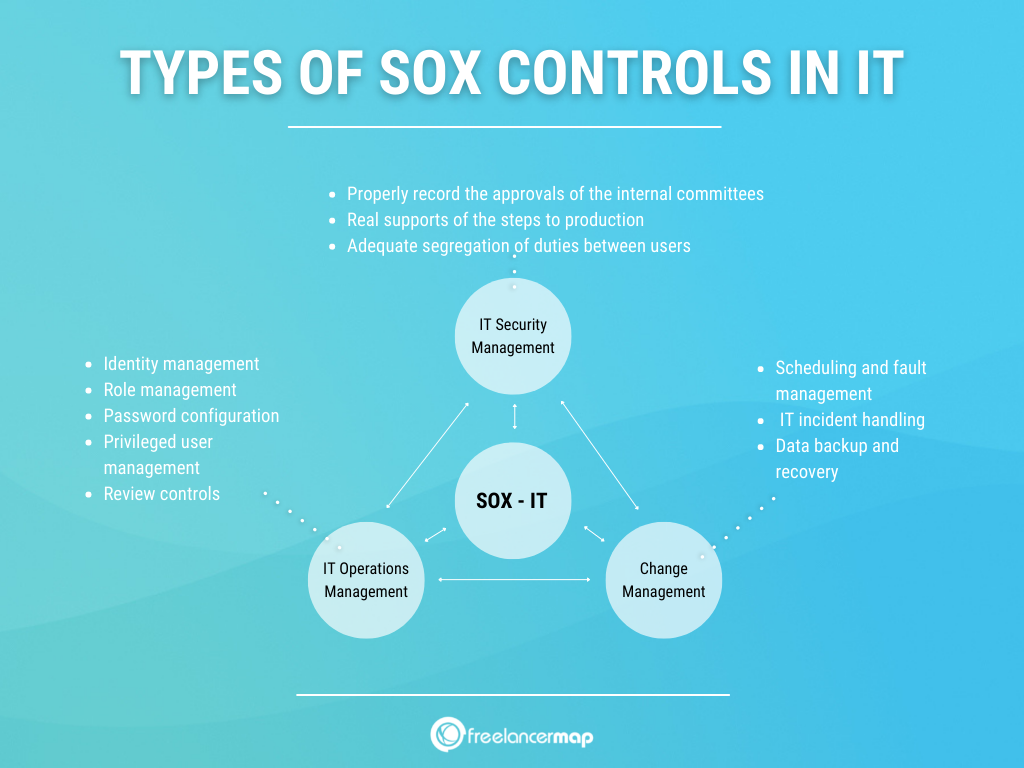

IT Security management
These controls seek to guarantee that the information is correctly safeguarded and with specific access privileges for employees who, according to their role or function, require access to financial information. To this end, different control activities are defined.
1.Identity management
This involves identity management procedures that ensure that the creation, modification and elimination of users in the information systems of the scope are carried out in accordance with the established procedures.
2. Role management
It is important to establish a periodic review of roles in the information systems, which verifies that the activities assigned to each role in the information systems are up to date and that the users who in turn have that role have the necessary powers to operate, without generating conflicts of segregation of functions.
3. Password configuration
This activity defines an adequate parameterisation of passwords in accordance with good practices and internal security procedures, seeking, among other things, that the information systems of the scope adequately restrict access through complex passwords.
4. Privileged user management
Implement controls that ensure the correct administration of privileged accounts, seeking that management guarantees the correct management of the users of the information systems administration systems. This is guaranteed by controlling the personnel with access to the passwords of these accounts, periodically changing their passwords and monitoring their transactionality.
5. Review controls
Finally, implement baseline security review controls on databases and operating systems, ensuring that management adequately secures its technology platform, in accordance with guidelines suggested by the Information Security or IT compliance areas.
Join our IT freelancer community today! Create your freelance profile in just 2 minutes.
Change management
These are those controls that seek to ensure that changes or modifications to the information systems covered by the SOX-IT scope comply with the policies and good software development practices attributed to this type of activities.
Such controls must comply with aspects such as:
- Properly record the approvals of the internal committees created to deploy a new development or change to the systems, always ensuring that the end-user tests and approvals of the requesting users are properly evidenced.
- That there are real supports of the steps to production or deployments on dates subsequent to their authorisation.
- Adequate segregation of duties between users with development and production privileges.
IT Operations Management
These procedures seek to ensure good practices in the operations environment. So that the information generated and processed is complete and always available to the business.
Controls typically considered for this domain are:
1. Scheduling and fault management for scheduled jobs or tasks 2.
Establish a proper formalisation, monitoring and response to problems related to the management of jobs or scheduled tasks for the information systems in scope.
2. IT incident handling
Adequate incident management according to internal procedures considering criticality, impact and service level agreements signed with the internal customer as well as with external suppliers.
3. Data backup and recovery
The implementation of information backup controls to ensure that information is always available according to business needs and to ensure good data restoration practices when necessary.
Data backup is another key area of focus that companies need to focus on. Assessing how a company backs their data is important in order to minimise business disruption and data loss. Hence, all original systems, data backups and standby systems must be in compliance with SOX requirements.
Sarbanes Oxley compliance: How do I comply with SOX in IT?
My organisation needs to comply with the SOX act, how do I start?
It is likely that your organisation is not ready to comply with SOX regulations in the first year. Which is why the industry regularly relies on specialised professionals. These professionals carry out a SOX pre-assessment exercise prior to formal certification.
This consists of internal work where a gap analysis is carried out to understand the current state of the organisation. The aim is to know what is in place in terms of implemented controls, partially implemented or those that do not work or do not exist and must be implemented from scratch.
In all cases, there should be structured action plans that will allow for timely follow-up of commitments.
It is also important that senior management commits to the implementation of these controls and periodically monitors or calibrates its teams to ensure that the SOX-IT controls implemented are working properly.
Finally, the internal audit teams will normally monitor and accompany the administrations. This is in order to ensure that they adequately comply with the controls through the periodic execution of tests, issuance of results and recommendations and permanent accompaniment.
Got any more questions about the SOX Act? Ask away below!
